When it comes to protecting your business from cyber threats, the biggest vulnerability might not be your software, firewalls or security tools, it is more often than not, your employees. Human error remains a leading cause of data breaches, from phishing attacks to poor password hygiene and mishandling of sensitive data. This alongside an ever-growing world of remote and hybrid work, means the risk employees pose to your data is only increasing.
Therefore, we have put together an article to explore why we know (from first-hand experience) that employees are often the weakest link in cyber security and how we can help businesses turn this risk into a strength with proper training and awareness.
Phishing Email Clicks
One of the most common cyber security pitfalls is falling for phishing emails. We send out simulation campaigns to our clients to ensure that they are always being tested and educated on their cyber security practices. In one of our recent phishing simulations many employees clicked on a suspicious link - some even submitted login credentials. These were not complex scams (they mimicked common formats like delivery notifications and fake alerts). The good news? We have been able to deliver targeted training based on real simulation results to those same companies to educate them further.
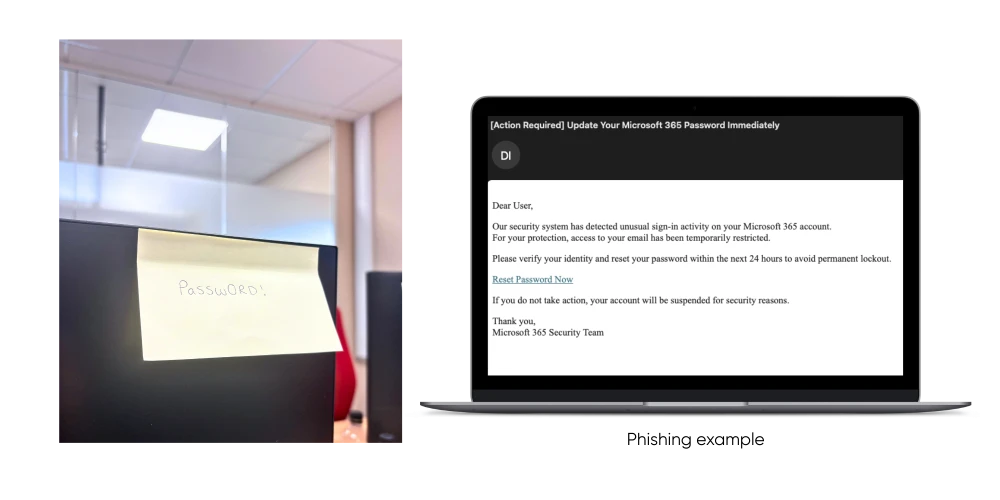
Weak Passwords and Password Reuse
Weak or reused passwords remain an open door for attackers. In several audits, we discovered repeated use of basic passwords like "Password123" or "Department2023" across multiple systems. These patterns were flagged through simple internal checks and highlighted in our reports. Once identified, we implemented password policy training and rolled out password management best practices, significantly improving credential hygiene within weeks.
We recommend password management systems (in particular Keeper Security) as they provide a secure, centralised platform for managing complex and unique passwords. Within Keeper, a feature called BreachWatch continuously monitors the dark web for exposed credentials and alerts users in real time if any of their passwords have been compromised, enabling swift action to protect their accounts. It also prompts users to address passwords that are considered weak, helping to strengthen overall security.
Use of Unsecured Personal Devices
With hybrid work now the norm, employees often access sensitive systems from personal devices (whether phones, laptops or tablets) without up-to-date antivirus protection, secure Wi-Fi connections, or the latest software updates. These devices are not managed by the company, meaning there is no direct control over the security of the device, the ability to remove business data if needed or prevent that data from potentially falling into the wrong hands. However, with the correct cyber security and awareness training, along with the rollout of secure access protocols, these vulnerabilities can be significantly reduced and effectively managed.
Mishandling Sensitive Data
From passwords on sticky notes to printed spreadsheets left unattended, mishandling sensitive data is surprisingly common. During one onsite assessment, we found password notes taped to desks in an open-plan office. Another client’s shared drive contained unencrypted files labelled with payroll data. We helped these businesses understand the risks through practical examples and awareness sessions, then guided them in adopting better data handling procedures – leading to real behavioural change. As part of this, we also introduced document labelling practices to clearly mark files as confidential or internal use only. This not only helps users recognise the sensitivity of the information but also triggers prompts when such files are attached to emails, reminding staff to consider whether it’s appropriate to share the document externally.
Multi-Factor Authentication, Conditional Access & Risk-Based Protection
MFA protects accounts by requiring multiple verification methods, such as a password and a device or biometric. This greatly reduces the risk of unauthorised access, even if credentials are compromised and is a crucial first step in account security. However, modern threats demand more. Conditional access policies strengthen security by assessing factors like location, device and behaviour before granting access. Risk-based user protection adds another layer, monitoring for suspicious activity and automatically triggering extra verification or blocking access when irregularities are detected. These measures reduce human error by automating threat detection and access controls, ensuring that even if users make mistakes (like falling for phishing or using weak passwords) security protocols still protect sensitive systems and data.

The Role of Cyber Security Awareness Training
Cyber security awareness training plays a critical role in reducing human error and strengthening a business's overall security posture. Regular, up-to-date training ensures that employees are continuously educated on the latest threats and best practices, helping them recognise and respond to phishing attempts, avoid weak password habits and handle sensitive data responsibly. Our experience with real-world phishing simulations has shown that untrained staff are far more likely to fall for basic scams - yet after tailored training sessions, those same teams demonstrated dramatic improvements in awareness and response times. By embedding cybersecurity education into company culture, businesses not only reduce the risk of breaches but also build a more resilient and proactive workforce ready to defend against advancing threats.
Cyber threats are evolving and so should your defences. Ready to strengthen your human firewall? Book a consultation today.
Tags:
Let us increase your productivity
Get in touch with us to arrange a FREE IT, Managed Print, Communications or Workflow Automation consultation.

